Generate and verify SLSA Provenance
You can use the Harness SSCA steps in Harness CI/CD pipelines to generate and verify SLSA Provenance.
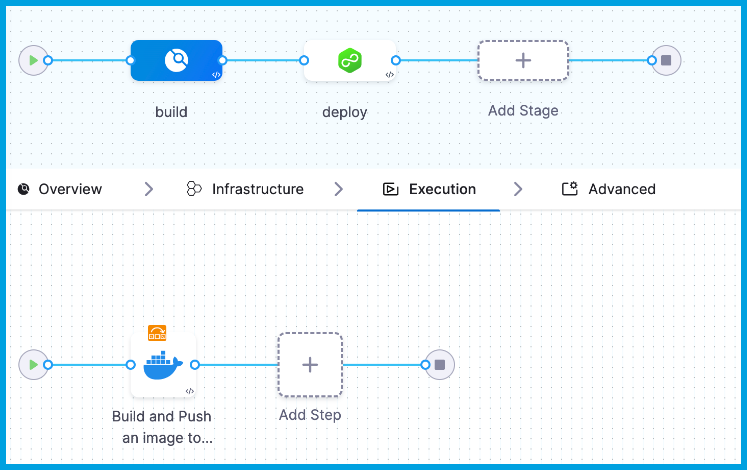
To complete this tutorial, you need a pipeline with a CI (build) stage and CD (deploy) stage. For example, the pipeline created in this tutorial has a Build stage with one step and a Deploy stage with two steps.
- Build stage:
- Build and Push an image to Docker Registry step: Build and push an image to a Docker registry.
- SLSA generation is enabled in the stage settings.
- Deploy stage:
- SLSA Verification step: Verify the SLSA Provenance.
- Rolling deployment step: Deploy the image.
This tutorial explains how to enable SLSA Provenance generation and configure an SLSA Verification step.
Generate a key pair
Keys are used to sign and verify provenance.
- Generate a public and private key pair. For example, you can use Cosign to generate key pairs.
- Create two Harness file secrets, one for the private key file and one for the public key file.
- Create a Harness text secret to store the password for the private key.
When your pipeline runs, the private key is used to sign the SLSA Provenance, and the public key is used to verify the provenance.
Generate SLSA Provenance
When you run a pipeline with SLSA generation enabled, Harness SSCA:
- Generates an SLSA Provenance for the image created by the Build and Push to Docker Registry step in the Build stage.
- Generates and signs an attestation using the provided key and password.
- Stores the SLSA Provenance in Harness and uploads the
.attfile to your container registry alongside the image.
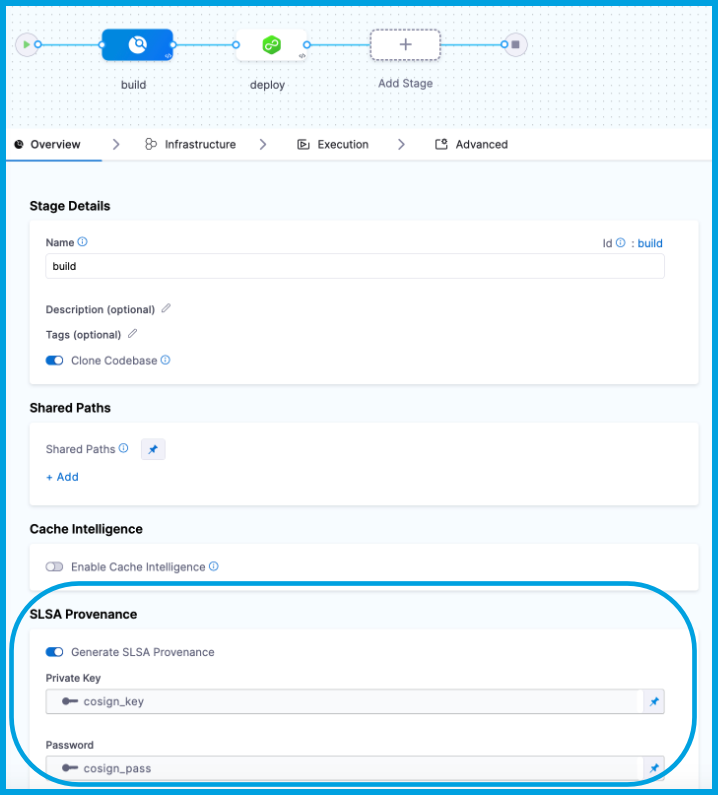
Enable SLSA Provenance generation in the Build stage settings.
- In your Harness pipeline, select the Build stage, and then select the Overview tab.
- Under SLSA Provenance, enable Generate SLSA Provenance.
- For Private Key, select the Harness file secret containing the private key file to use to sign the attestation.
- For Password, select the Harness text secret containing the password for the private key.
To generate SLSA Provenance, you must use the Build and Push to Docker Registry step to build and push your image. Support for other Build and Push steps is coming soon.
Create policies
You must create a set of OPA policies that you want Harness SSCA to use for SLSA Provenance verification. You can create a dedicated SLSA Provenance verification policy set or use existing policy sets that you've already created. For more information about creating policies in Harness, go to the Harness Policy As Code overview.
OPA polices used for SLSA Provenance verification are different from SSCA policies used for SSCA policy enforcement.
In your Harness Project, under Project Setup, go to Policies. You can also create policies at the Account and Org scopes.
Select Policies, and then create policies for the individual rules that you want to enforce.
You can select from the policy library or write your own policies. This tutorial enforces the following policies:
package slsa
# Build repo must be 'https://github.com/abc/abc-sample'. SLSA verification fails if a different repo is detected.
deny[msg]{
input[0].outcome.stepArtifacts.provenanceArtifacts[0].predicate.buildDefinition.externalParameters.codeMetadata.repositoryURL != "https://github.com/abc/abc-sample"
msg := "Repository verification failed in Provenance"
}
# Build branch must be 'main'. SLSA verification fails if a different branch is detected.
deny[msg]{
input[0].outcome.stepArtifacts.provenanceArtifacts[0].predicate.buildDefinition.externalParameters.codeMetadata.branch != "main"
msg := "Branch verification failed in provenance"
}For more examples, go to Policy samples.
Create policy sets to group related policies. You must have at least one policy set.
Verify provenance
The SLSA Verification step does the following:
- Verifies the authenticity of the attestation.
- Verifies the provenance data by applying the specified policy set.
- Records the policy evaluation results in the step's logs.
- Reports the overall pass/fail for SLSA verification on the Artifacts tab.
Add the SLSA Verification step to your Deploy stage. This is a container step that must be inside a container group.
Enter a Name for the step.
For Container Registry, select the Docker Registry connector that is configured for the Docker-compliant container registry where the artifact is stored, such as Docker Hub, Amazon ECR, or GCR.
If you're using Docker-compliant ECR or GCR repositories, you must configure your Docker Registry connector as a valid artifact source.
- For ECR, go to Use Docker Registry for ECR.
- For GCR, go to Use Docker Registry for GCR.
For Image, enter the repo path (in your container registry) for the image that you want to verify, such as
my-docker-repo/my-artifact.For Docker-compliant ECR or GRC repositories, provide the full URI for the image, such as
1234567890.dkr.ecr.REGION.amazonaws.com/IMAGE_NAME:TAG.For Tag, enter the tag for the image, such as
latest.For Public Key, select the Harness file secret containing the public key to use to verify the authenticity of the attestation.
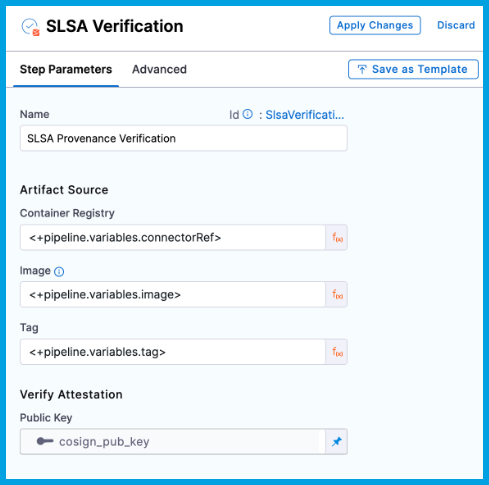
On the Advanced tab for the SLSA Verification step, expand the Policy Enforcement section, and then add your SLSA Provenance verification OPA policies.
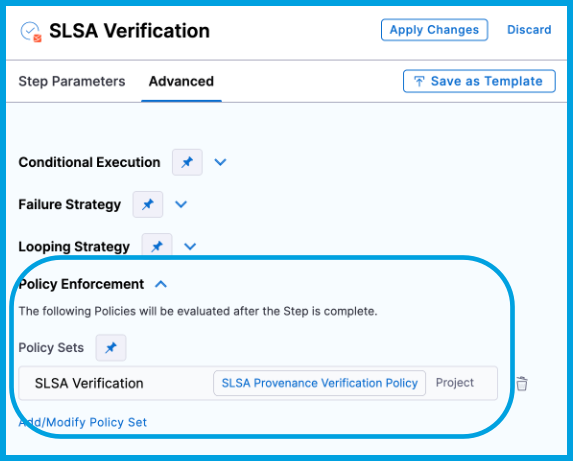
View attestations and violations
When the pipeline runs, the SLSA Provenance is generated and the attestation is signed. The signed attestation is stored, as an .att file, in the artifact repository along with the image.
When viewing the Execution details page in Harness, you can view and download the SLSA Provenance from Artifact Type column on the Artifacts tab.
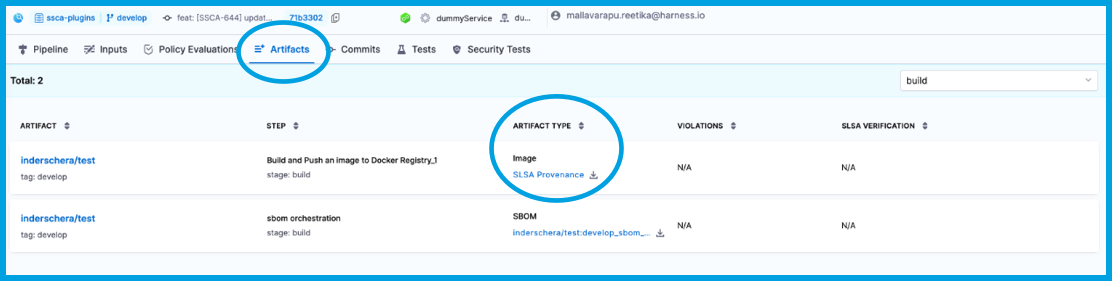
If your pipeline has multiple stages, the Artifacts tab is filtered by stage. Use the dropdown menu to select the relevant stage.
In the SLSA Verification column on the Artifacts tab, you can see if the verification passed or failed.
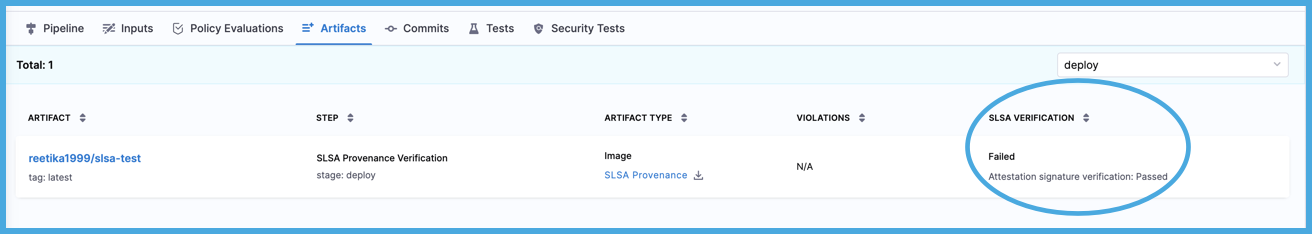
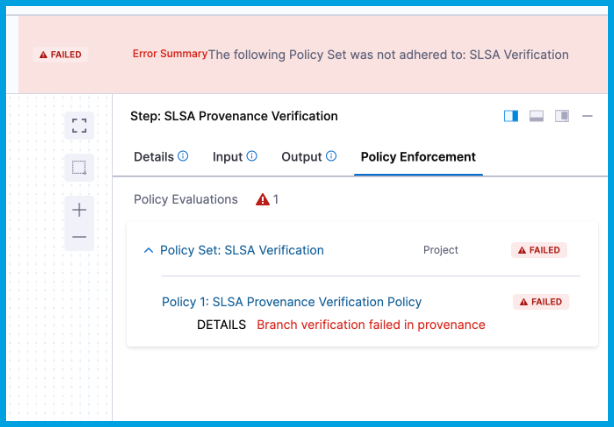
To inspect which policies failed, select the Pipeline tab, select the SLSA Verification step, and then select the Policy Enforcement tab.